CalendarSpark is a browser extension developed by MindSpark. This extension allows an easy way to print or view calendar templates and make schedulers for a day/week/month/year.
This browser extension hijacks your browser home page and search engine, changing them to MyWay.com. While the extension is installed it monitors your browsing activity and collets visited websites, clicked links, and sometimes even personal information, which it later uses to display targeted unwanted ads through your browsing sessions.
While browsing the internet with this extension installed you will see additional sponsored links, ads, and sometimes even pop-up ads on websites that are not supposed to have any of these. Several anti-virus scanners have detected this extension as a Browser Hijacker, and due to its data collecting behavior, it is not recommended to keep it on your computer.
About Browser Hijackers
Browser hijackers (sometimes called hijackware) are a kind of malware that modifies web browser configuration settings without the computer owner’s knowledge or permission. These kinds of hijacks are raising at an alarming rate across the world, and they could be truly nefarious and sometimes harmful too. Browser hijacker malware is created for a number of reasons. These are generally used to force hits to a specific site, manipulating web traffic to generate ad revenue. However, it’s not that harmless. Your online safety is jeopardized and it is also extremely irritating. In a worst-case scenario, your browser could be hijacked to open up your computer system to a host of additional attacks.
Indications of browser hijack
When your browser is hi-jacked, the following could happen: your home page is reset to some unknown webpage; you get redirected to sites you never intended to visit; The default search page of the web browser is changed; unwanted new toolbars are added to your internet browser; you’ll find random pop-ups start showing on a regular basis; your internet browser starts running slowly or exhibits frequent errors; Inability to navigate to certain websites, particularly antivirus as well as other security software sites.
Exactly how browser hijacker finds its way onto your PC
Browser hijackers can enter a PC by some means or other, including via file sharing, downloads, and e-mail as well. They could also be deployed via the installation of an internet browser toolbar, add-on, or extension. A browser hijacker can be installed as a part of freeware, shareware, demoware, and pirated programs. An example of some well-known browser hijacker includes Conduit, Anyprotect, Babylon, DefaultTab, SweetPage, RocketTab, and Delta Search, but the names are regularly changing.
Browser hijackers could interrupt the user’s web surfing experience significantly, track the websites visited by users and steal sensitive information, cause problems in connecting to the net, and then finally create stability issues, causing programs and computers to freeze.
Removal
Some kinds of browser hijackers can be quickly removed from the computer by deleting malicious applications or any other recently added freeware. Regrettably, most of the software applications used to hijack an internet browser are intentionally designed to be difficult to remove or detect. Furthermore, manual removals require in-depth system knowledge and therefore can be an extremely difficult job for novice computer users.
What you can do if Virus Stops You From Downloading Antivirus?
Practically all malware is inherently dangerous, but certain types of malware do much more damage to your computer than others. Some malware sits in between your computer and your internet connection and blocks a few or all websites that you would like to check out. It will also block you from the installation of anything on your PC, especially antivirus applications. If you’re reading this article now, you might have perhaps realized that virus infection is the real cause of your blocked net connectivity. So how to proceed when you want to download and install an antivirus application like Safebytes? Although this sort of problem can be tougher to circumvent, there are some steps you can take.
Download the software in Safe Mode with Networking
In Safe Mode, you may change Windows settings, un-install or install some program, and eliminate hard-to-delete viruses and malware. In case the virus is set to load immediately when the PC starts, switching to this mode can prevent it from doing so. To boot into Safe Mode, press “F8” key on the keyboard just before Windows logo screen appears; Or after normal Windows boot up, run MSCONFIG, look over Safe Boot under Boot tab, and then click Apply. After you reboot into Safe Mode with Networking, you could download, install, as well as update the anti-malware program from there. At this point, you can run the anti-malware scan to eliminate viruses and malware without hindrance from another application.
Obtain the antivirus program using an alternate web browser
Some malware only targets particular internet browsers. If this sounds like your situation, utilize another browser as it may circumvent the virus. The best way to avoid this problem is to choose a browser that is well known for its security features. Firefox has built-in Phishing and Malware Protection to help keep you safe online.
Install and run anti-malware from the Thumb drive
Here’s yet another solution which is creating a portable USB antivirus software package that can check your system for malicious software without the need for installation. To run anti-virus from a USB drive, follow these simple steps:
1) Use another virus-free PC to download Safebytes Anti-Malware.
2) Plug in the flash drive to a USB slot on the clean computer.
3) Double-click the executable file to open the installation wizard.
4) When asked, choose the location of the USB drive as the place where you would like to store the software files. Follow activation instructions.
5) Unplug the flash drive. You may now use this portable anti-malware on the affected computer.
6) Run the Safebytes Anti-malware directly from the flash drive by double-clicking the icon.
7) Run Full System Scan to detect and clean-up up all types of malware.
SafeBytes Anti-Malware Benefits
If you are looking to install anti-malware software for your PC, there are numerous tools on the market to consider but you cannot trust blindly to anyone, irrespective of whether it is free or paid software. A few of them are great, some are decent, while some will harm your computer themselves! You need to select one that is dependable, practical, and has a strong reputation for its malware protection. While thinking about the dependable software programs, Safebytes AntiMalware is certainly the strongly recommended one.
SafeBytes anti-malware is a trusted tool that not only protects your computer system permanently but is also very user-friendly for people of all ability levels. Once you’ve got installed this software, SafeByte's sophisticated protection system will make sure that absolutely no viruses or malicious software can seep through your personal computer.
SafeBytes has a plethora of amazing features that can help you protect your PC from malware attacks and damage. Listed below are some of the great features included in the tool.
Optimum AntiMalware Protection: Using a critically acclaimed malware engine, SafeBytes provides multilayered protection that is designed to find and eliminate viruses and malware that are concealed deep in your computer’s operating system.
Live Protection: SafeBytes offers a completely hands-free real-time protection that is set to observe, block, and wipe out all computer threats at its very first encounter. It will inspect your computer for suspicious activity regularly and its unparalleled firewall shields your computer from illegal entry by the outside world.
Faster Scan: SafeBytes Anti-Malware has got a multi-thread scan algorithm that works up to 5 times faster than any other protection software.
Website Filtering: SafeBytes checks and provides a unique safety ranking to each and every site you visit and block access to webpages known to be phishing sites, thus safeguarding you from identity theft, or known to contain malware.
Light-weight: The program is light-weight and will work silently in the background, and will not impact your computer efficiency.
Premium Support: For any technical inquiries or product assistance, you could get 24/7 professional assistance via chat and email.
Technical Details and Manual Removal (Advanced Users)
To get rid of CalendarSpark manually, navigate to the Add/Remove programs list in the Windows Control Panel and select the program you want to get rid of. For browser extensions, go to your web browser’s Addon/Extension manager and select the add-on you intend to remove or disable. You will probably also want to reset your internet browser.
In order to ensure the complete removal, manually examine your hard disk and computer registry for all of the following and remove or reset the values accordingly. But bear in mind, this is a tricky task and only computer professionals can carry it out safely. In addition, certain malicious programs are capable to defend against its deletion. Doing this malware-removal process in Safe Mode is suggested.
Files:
calendarspark.dl.myway[1].xml
%UserProfile%\Local Settings\Application Data\CalendarSparkTooltab
chrome-extension_apfkjcjglfhoemadfobgcacfkdhapiab_0.localstorage-journal
%LOCALAPPDATA%\CalendarSparkTooltab
http_calendarspark.dl.tb.ask.com_0.localstorage-journal
http_calendarspark.dl.tb.ask.com_0.localstorage
Calendarspark.exe 310,048 602097e5efa71f01dca1ad60ba108730
%UserProfile%\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\lacjhcgjigifchcapcccoippjdnkbagj
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Extensions\lacjhcgjigifchcapcccoippjdnkbagj
www.calendarspark[1].xml
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\lacjhcgjigifchcapcccoippjdnkbagj
Registry:
HKEY_CURRENT_USER\Software\CalendarSpark
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry\DOMStorage\calendarspark.com
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry\DOMStorage\calendarspark.dl.myway.com
HKEY_CURRENT_USER\Software\Wow6432Node\CalendarSpark
HKEY_CURRENT_USER\Software\Google\Chrome\PreferenceMACs\Default\extensions.settings, value: lacjhcgjigifchcapcccoippjdnkbagj
HKEY_LOCAL_MACHINE\Software\[APPLICATION]\Microsoft\Windows\CurrentVersion\Uninstall..Uninstaller
CalendarSparkTooltab Uninstall Internet Explorer


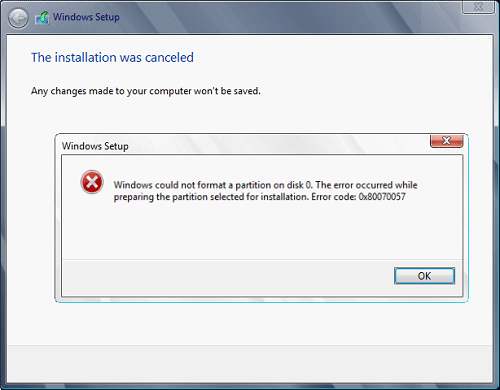 This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.
This error is very frustrating and it annoys pretty much anyone who encountered it but do not worry we have a solution for you.
First thing is to confirm the error prompt, Click on the OK button and then on X to exit Windows 10 installation wizard. Click on yes to confirm that you want to exit the setup.
You will find yourself in original installation windows.
On that screen choose and click on Repair your computer. Choose an option screen that will pop up, click on Troubleshoot. In the advanced options, click on the command prompt.
Once you are in command prompts type DISKPART and hit ENTER
In the diskpart prompt type LIST DISK and hit ENTER again.
type SELECT DISK #, where # is listed disk number where you would like to install Windows.
type LIST VOLUME in order to list volumes in the selected disk and hit ENTER
You need to select the volume on which you would like to place your WINDOWS, to do this type in SELECT VOLUME #, where # is the listed number of the volume
Finally, type FORMAT FS=NTFS and hit ENTER
You have successfully formated a given volume, you can now exit DISKPART and return to setup, to exit DISKPART simply type exit and hit ENTER.
Leave command prompt as well by again typing exit and hitting ENTER
You will be returned to Choose an option screen, click on Turn off your PC.
Your drive has been successfully formatted and it is ready for clean Windows installation, you can now restart your Windows 10 installation and the process will complete without errors.  You can it here:
You can it here: 