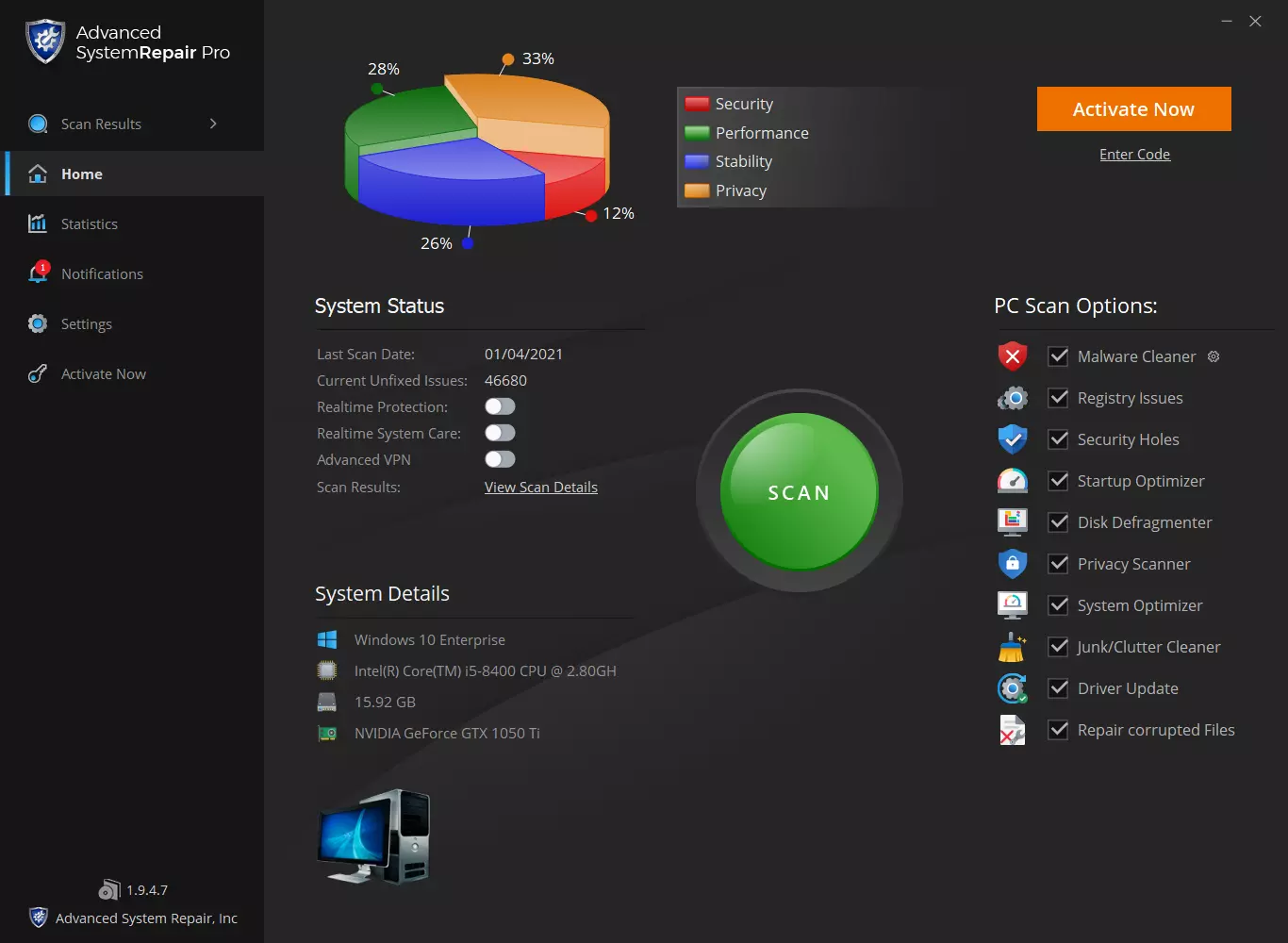
FindYourMaps is a Google Chrome Browser Extension developed by Mindspark. This extension hijacks your home page and new tab page changing them to MyWebSearch.com in order to display ads more efficiently.
While using this extension you will see additional pop-up ads, sponsored content, and unwanted ads (that are sometimes not ever relative to your search query) displayed throughout your browsing sessions, cluttering up the pages and sometimes even going over page parts, making some pages unreadable.
Several anti-virus applications have marked this Extension as a Browser Hijacker due to its data mining behaviors and ad injections and were marked for removal by most of them.
About Browser Hijackers
Browser hijacking is a very common type of internet fraud where your web browser configurations are modified to allow it to do things you never intend. Practically most browser hijackers are made for advertising or marketing purposes. These are typically used to force visitors to a specific website, manipulating web traffic to generate ad revenue. However, it is not that innocent. Your web safety is jeopardized and it is extremely annoying. What’s more, hijackers will make the whole infected system fragile – other harmful malware and viruses would use these opportunities to get into your system very easily.
Indications of browser hijack
There are many symptoms that indicate the browser is highjacked: your home page is reset to some unknown site; you observe new unwanted favorites or bookmarks added, typically directed to ad-filled or porn websites; The default search page of your web browser is modified; you see many toolbars on the browser; you observe numerous ads show up on the browsers or display screen; your browser has instability issues or displays frequent errors; you cannot go to specific sites such as home pages of security software.
How it infects your computer
A browser hijacker could be installed on your PC when you check out an infected website, click an e-mail attachment, or download something from a file-sharing website. They also come from add-on programs, also known as browser helper objects (BHO), web browser plug-ins, or toolbars. A browser hijacker could also come bundled up with some free application which you inadvertently download and install the browser hijack, compromising your PC security.
Browser hijackers can record user keystrokes to gather potentially invaluable information leading to privacy concerns, cause instability on computers, drastically disrupt user’s browsing experience, and ultimately slow down the system to a point where it will become unusable.
How to fix a browser hijack
The one thing you can try to remove a browser hijacker is to locate the malware inside the “Add or Remove Programs” list of the Windows Control Panel. It may or may not be there. When it is, uninstall it. But, many hijacking codes aren’t very easy to remove manually, as they go much deeper into your operating system. On top of that, manual removal demands you to carry out several time-consuming and tricky procedures that are very hard to carry out for novice computer users.
Anti-malware application is incredibly efficient when it comes to picking up and eliminating browser hijackers that standard anti-virus software has overlooked. Safebytes Anti-Malware features a state-of-the-art anti-malware engine to help you avoid browser hijacking in the first place, and clean up any pre-existing problems. Along with the anti-virus tool, a system optimizer, like SafeBytes’s Total System Care, could help you in deleting all associated files and modifications in the computer registry automatically.
What you can do if Virus Stops You From Downloading Or Installing Anything?
Viruses may cause a great deal of damage to your computer. Certain malware goes to great lengths to stop you from downloading or installing anything on your computer system, particularly antivirus programs. If you’re reading this now, you have probably realized that a malware infection is a reason behind your blocked net connectivity. So how to proceed when you want to download and install an anti-virus application such as Safebytes? Do as instructed below to get rid of the malware by alternate methods.
Start Windows in Safe Mode
If any virus is set to load automatically when Windows starts, stepping into Safe Mode could very well block this attempt. Since only the minimum applications and services start-up in Safe Mode, there are seldom any reasons for conflicts to occur. Below are the steps you have to follow to remove malware in Safemode.
1) At power-on/startup, press the F8 key in one-second intervals. This should bring up the Advanced Boot Options menu.
2) Use the arrow keys to choose Safe Mode with Networking and hit ENTER.
3) When this mode loads, you should have an internet connection. Now, utilize your browser to download and install Safebytes.
4) As soon as the application is installed, allow the scan run to remove trojans and other threats automatically.
Obtain the anti-malware program in an alternate internet browser
Some malware might target vulnerabilities of a specific browser that obstruct the downloading process. If you are not able to download the security program using Internet Explorer, this means malware is targeting IE’s vulnerabilities. Here, you must switch to another internet browser like Chrome or Firefox to download the Safebytes application.
Run anti-virus from your pen drive
Another option would be to create a portable antivirus program onto your USB stick. Adopt these measures to employ a flash drive to fix your infected computer system.
1) Download the anti-malware program on a virus-free computer.
2) Plug the Flash drive into the uninfected computer.
3) Double-click the Setup icon of the anti-malware software to run the Installation Wizard.
4) Choose the USB flash drive as the location for saving the file. Follow the directions to finish the installation process.
5) Now, plug the thumb drive into the infected computer.
6) Double-click the Safebytes Anti-malware icon on the pen drive to run the program.
7) Click on “Scan Now” to run a complete scan on the affected computer for viruses.
Highlights of SafeBytes Anti-Malware
These days, an anti-malware program can protect your laptop or computer from different forms of online threats. But how do choose the right one amongst several malware protection software that’s available out there? Perhaps you might be aware, there are numerous anti-malware companies and tools for you to consider. A few of them are great and some are scamware applications that pretend as legitimate anti-malware programs waiting around to wreak havoc on your personal computer. You have to be careful not to pick the wrong application, particularly if you purchase a paid software. One of the highly recommended software by industry experts is SafeBytes Anti-Malware, well-known security software for Windows computers.
Safebytes is among the well-established PC solutions firms, which offer this comprehensive anti-malware program. Through its cutting-edge technology, this software will help you protect your computer against infections caused by different types of malware and similar internet threats, including spyware, adware, trojans, worms, computer viruses, keyloggers, potentially unwanted program (PUPs), and ransomware.
SafeBytes has great features when compared with various other anti-malware programs. These are some of the great features included in the tool.
Real-time Threat Response: SafeBytes delivers complete and real-time security for your PC. They are extremely efficient in screening and getting rid of different threats because they are continuously revised with the latest updates and safety measures.
World-class AntiMalware Protection: By using a critically acclaimed anti-malware engine, SafeBytes offers multilayered protection which is made to find and eliminate viruses and malware which are hidden deep in your computer’s operating system.
Web Filtering: Safebytes allots all websites a unique safety rating that helps you to have an idea of whether the webpage you’re about to visit is safe to view or known to be a phishing site.
Very Low CPU and RAM Usage: SafeBytes is a lightweight tool. It consumes a very small amount of processing power as it runs in the background so you are free to use your Windows-based computer the way you want.
24/7 Assistance: SafeBytes provides 24/7 technical support, automatic maintenance, and upgrades for the best user experience.
To sum it up, SafeBytes Anti-Malware offers outstanding protection combined with very low system resource usage with great malware prevention and detection. You can rest assured that your PC will be protected in real-time once you put this software program to use. You will get the very best all-around protection for the money you pay on SafeBytes anti-malware subscription, there is no doubt about it.
Technical Details and Manual Removal (Advanced Users)
If you don’t wish to use an automated tool and prefer to eliminate FindYourMaps manually, you could do so by going to the Windows Add/Remove Programs menu in the control panel and deleting the offending software; in cases of web browser add-ons, you can remove it by visiting the browser’s Add-on/Extension manager. It’s also advised to factory reset your web browser settings to their default state.
To ensure the complete removal, manually examine your hard drive and Windows registry for all of the following and remove or reset the values as needed. Please be aware that this is for experienced users only and might be challenging, with incorrect file removal causing additional PC errors. Furthermore, some malware is capable of replicating itself or preventing deletion. Completing this task in Safe Mode is recommended.
 Bluetooth perhaps is slowly becoming an outdated feature but sometimes you can really used it and need it.
By default, in Windows 11 Bluetooth is turned OFF so if you need it, you will need to turn it ON first. Luckily turning it ON is easy and we will guide you through the process
Bluetooth perhaps is slowly becoming an outdated feature but sometimes you can really used it and need it.
By default, in Windows 11 Bluetooth is turned OFF so if you need it, you will need to turn it ON first. Luckily turning it ON is easy and we will guide you through the process
 Razer is a well-known brand among PC gamers and users, it started as a peripheral manufacturer focused on keyboards and mouse but after years passed Razer expanded its inventory offerings. It soon started offering headphones and lately has branched into wider product lines like gaming chairs and protection masks.
Razer is a well-known brand among PC gamers and users, it started as a peripheral manufacturer focused on keyboards and mouse but after years passed Razer expanded its inventory offerings. It soon started offering headphones and lately has branched into wider product lines like gaming chairs and protection masks. Most interesting for me personally is Razers Katana, the power supply unit. It is a modular power supply ranging from 750W to 1200W with the additional option of Titanium rated one with an impressive 1600W of power. Power supply will start shipping in early 2022 and at the time of writing this article no price range has been released.
Most interesting for me personally is Razers Katana, the power supply unit. It is a modular power supply ranging from 750W to 1200W with the additional option of Titanium rated one with an impressive 1600W of power. Power supply will start shipping in early 2022 and at the time of writing this article no price range has been released.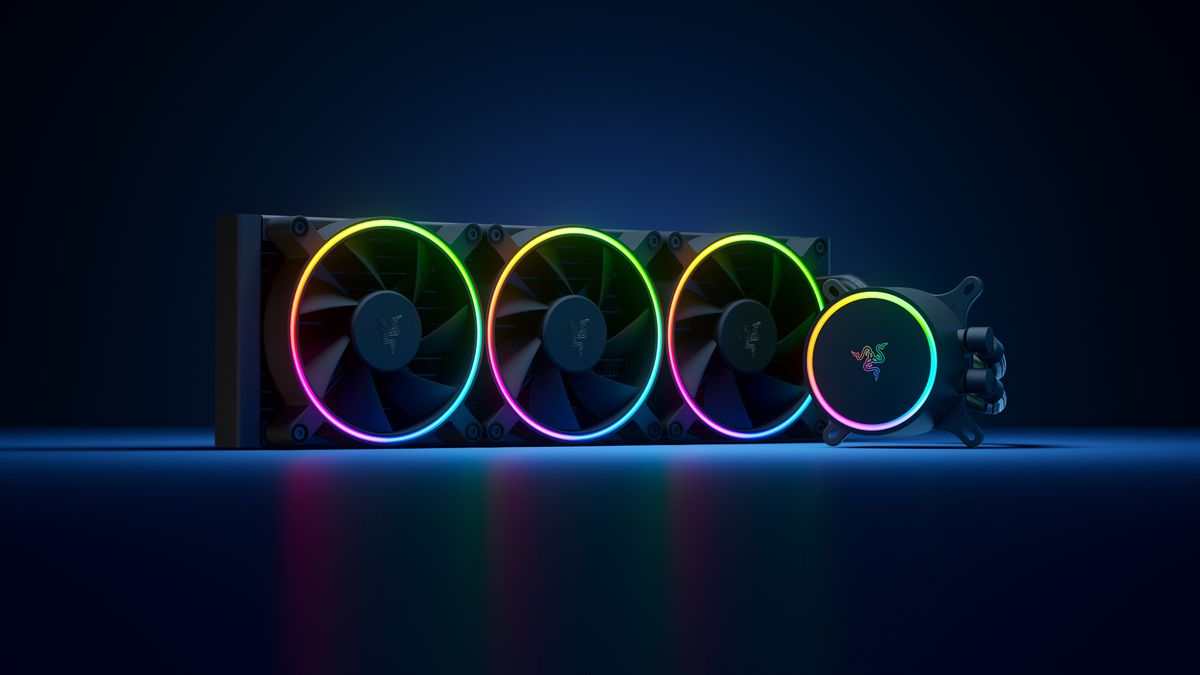 Hanbo liquid cooler will feature an optimized intake design so it can ensure greater heat transfer and fluid dynamic for improved reliability and silent operation. Radiator comes in 240mm size with two fans and a larger one of 360mm with three fans. The pump will be able to rotate in any direction of full 360 degrees so it can fit in any case. Hanbo will be released in November this year but no pricing has been released so far.
Hanbo liquid cooler will feature an optimized intake design so it can ensure greater heat transfer and fluid dynamic for improved reliability and silent operation. Radiator comes in 240mm size with two fans and a larger one of 360mm with three fans. The pump will be able to rotate in any direction of full 360 degrees so it can fit in any case. Hanbo will be released in November this year but no pricing has been released so far. Kunai fans will boast high static pressure performance with lowered noise. They will go as far as 2200rpm for the 120mm version where the 140mm version will go up to 1600rpm. They will come with addressable LEDs and up to eight fans will be able to be connected to Razer’s PWM fan controller that will come with a magnet at the back for easy attachment to any steel part of PC casing.
Kunai fans will boast high static pressure performance with lowered noise. They will go as far as 2200rpm for the 120mm version where the 140mm version will go up to 1600rpm. They will come with addressable LEDs and up to eight fans will be able to be connected to Razer’s PWM fan controller that will come with a magnet at the back for easy attachment to any steel part of PC casing.